A Man in the middle attack occurs when hackers secretly position themselves between two online communicating parties. In this way, they read the messages and pass them by modifying the messages, without letting any of the other parties know.
In this blog, we will discuss what the MITM attack is, its types, how to detect and prevent them, and much more related to Man-in-the-middle Attacks.
Man In The Middle Attack: Meaning
A Man in the middle attack attack is a type of cyberattack in which personal, confidential or sensitive information is stolen by hackers by eavesdropping on communication between two online parties. It can be a communication between a user and a web application.
The most common types of MITM attacks taking place nowadays are the ones in which the attackers steal credit card numbers, account information, and login credentials to steal money and make unauthorised purchases using your account.
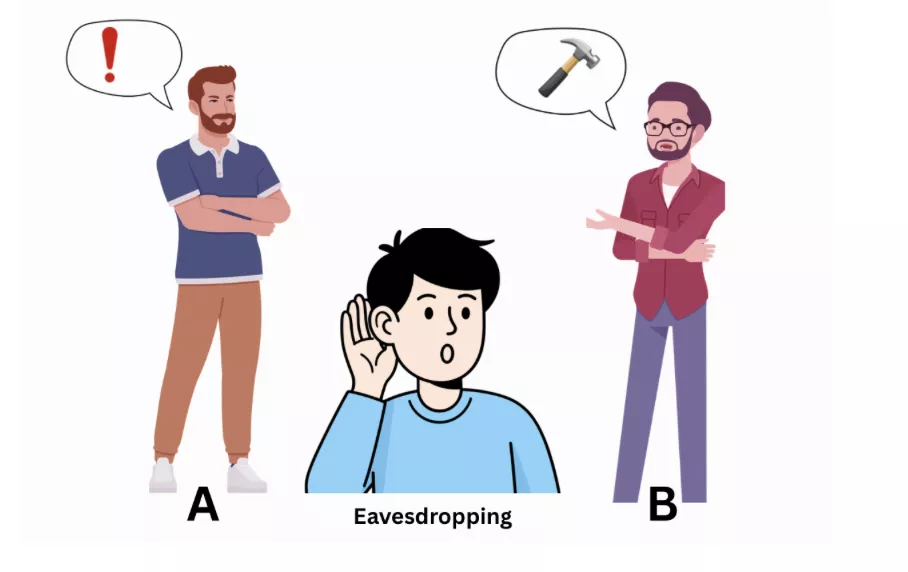
A Man in the middle attack includes eavesdropping on someone’s personal communication. In this case of a MITM attack, the hacker will read your messages and alter them before they reach the other person without letting you or the other person know.
Read More: Cyber Attack – Common Cyberthreats You Must Know in 2025
How Does An MITM Attack Work? (with Example)
The working of an MITM attack is where most people are confused. Let’s understand it in just 3 simple steps.
- A person sends a message to another.
- The Man in the middle attack attacker intercepts the message without letting either of the persons know.
- The hacker alters or changes the message before it reaches the other person.
Basically, a Man-in-the-Middle attack is a process that takes place due to the eavesdropping on communication between two people. Let’s understand it better with the help of an example.
Let’s suppose you are ‘A’ and you sent a message to ‘B’ (one of your friends). Before your message reaches B, it is altered without your or B’s knowledge. This is done by hackers by accessing your accounts secretly.
Example of ‘Equifax’
One of the most famous Man-in-the-Middle attacks that took place was the Equifax attack. It is among the three largest credit history companies.
The company went through an MITM data breach in 2017, which made approximately 100-150 million customers suffer, as the data breach led to the exposure of the financial data of the customers to cyber criminals.
Read More: What is Cybersecurity? Principles & Attacks
Stages Of An MITM Attack
There are two main stages of a Man in the middle attack , interception and decryption. The cyber criminals intercept the data that is being transferred from one person to another and then decrypt the information.
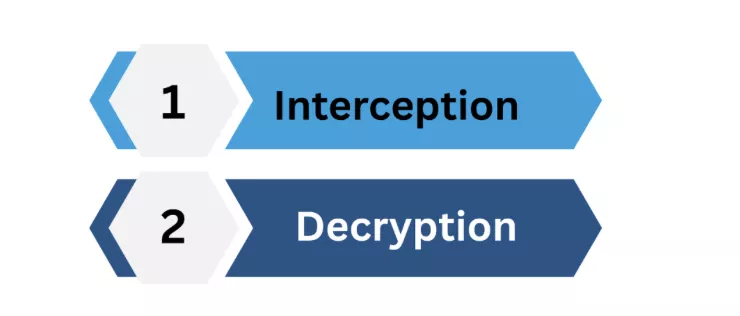
1. Interception
If a hacker wants to get in the middle of a conversation between a user and a web application, then an attacker will have to intercept the data that is traveling between them. The attackers then pass the information among the victims in such a natural way that it looks real, and they don’t suspect anything.
2. Decryption
You know almost all the genuine internet communications are encrypted today. So MITM hackers need to decrypt the data before using it. Cyber hackers perform the decryption by stealing encryption keys, IP spoofing, and by various other methods or types that we will discuss next.
Types Of Man-in-the-Middle Attacks
There is not just one way a Man in the middle attack is done. There are various ways and types of these attacks that hackers use to steal the information. Check them below.
1. Email Hijacking

Email Hijacking is a type of Man-in-the-Middle attack in which attackers get control of the bank’s email accounts, which lets them track the transaction history and patterns.
They also send customers emails for sharing their account details, login credentials, or in some cases, they can even ask you to share money.
Read More: What is Email Writing? Why It Is Important, Examples & Strategies
2. DNS Spoofing
DNS Spoofing refers to Domain Name System Spoofing. It is a cyberattack in which you are redirected to a fake or spoofed website or application by manipulating the DNS records of a website. You wouldn’t even know the difference because the spoofed websites are designed and created exactly the same, which makes you believe it is the original one.
When you’ll open the application or website, they’ll somehow convince you to make a payment or enter your details, and there you will lose all your money.
3. IP Spoofing

IP Spoofing is another type of Man in the middle attack , which is somewhat similar to DNS Spoofing. In IP Spoofing, the MIMT attacker modifies and makes changes to the URL of the fake website in such a way that it looks real, so people can’t differentiate and suspect if it’s fake.
4. Wi-Fi Eavesdropping
Wi-Fi Eavesdropping is a method to hack your devices and steal information by getting them connected to wireless networks. Cyber criminals set up password-free public Wi-Fi networks so that people can easily connect to them for getting connectivity, but in reality, it is just a trap.
Also, I would suggest that you always turn off the auto-connect Wi-Fi feature to prevent these scams.
5. Stealing Browser Cookies
Browser cookies refer to the data collected by a web browser to enhance the user experience. It stores your information so you don’t have to enter the same information like your first name, last name, phone number, etc, again and again.
Browser cookies are stolen by combining other MITM attack techniques. For example, a cyber criminal can get access to a user’s device through Wi-Fi Eavesdropping and then steal browser cookies and gain access to passwords, credit card details, phone numbers, and other sensitive information.
Read more: Cyber Security Terms You Must Know: 35+ Essentials for Every Learner
6. SSL Hijacking
Secure Socket Layer (SSL) can be hijacked, which is responsible for encrypting web browser and the server using the SSL certificates. The Man in the Middle attack misleads the encryption using fake SSL certificates to hijack the process and exploit data encryption.
7. HTTPS Spoofing
HTTPS spoofing is a method in which a man-in-the-middle attack makes a user land on an HTTP page without encryption to get access to unprotected data. Hyper Text Transfer Protocol is responsible for a safer communication experience for users by giving them strong encryption.
How To Detect An MITM Attack?
For detecting MITM attacks, you need to follow certain protocols, including both human and technical. Let’s check out some of the most common signs that you’ll see if you have become a victim of a Man-in-the-Middle cyber attack.
1. Unsecured Wi-Fi

If you notice an unsecured, public Wi-Fi, other than the municipal Wi-Fi, then you must not connect to it, as it may lead to your device getting hacked. You may get free connectivity, but remember, then all of your activities will be monitored too.
2. Strange URLs
If you notice any strange URL that is not of any recognizable official website, then it could be a spoofed website. You must carefully check the webpages and URLs before filling out any of your personal information.
3. Unusual Disconnections
If you are getting disconnected from a page again and again, then it may be a situation of an MITM attack. If an attacker is performing a MITM attack, then this may be a chance for hackers to steal your information, as you will have to enter your login credentials like your username and password, again and again.
Read More: Free IBM Cybersecurity Online Internship With Certificate 2025: An Effective Guide
How To Prevent a Man In the Middle Attack ?
Are you curious to learn about how you can prevent Man-in-the-Middle attacks? Then you’ve just reached the right place. Some of the key points for preventing MITM attacks are listed down. Check them below.
- Update and use secured networks: You should always keep updating your Wi-Fi systems and network connections and always make sure to use only secured networks.
- Use strong passwords: Make sure that the passwords you use are strong with a mix of lowercase and uppercase characters, along with some special characters and numbers.
- Thoroughly check webpages and URLs: Whenever you visit any website, the first task that you must do is to thoroughly check the webpage and the URL. If anything seems suspicious, immediately back off. Never perform action-oriented tasks like sending money or making a purchase from the webpages you are unsure about.
- Install antivirus software: You can also install antivirus software. This is one of the most basic cybersecurity practices but it can make a huge difference. Antivirus software can help protect your device from viruses and attacks.
Learn Cybersecurity With PW Skills
Enroll in PW Skills Certified Payment Security Professional Program from leaders at PW Skills in collaboration with Panacea Infosec. Get industry expert led training, capstone projects, and On the Job Training based on a 12 week apprenticeship program.
Get job opportunity at Panacea Infosec after the OJT completion, along with certification from PW Skills and proficiency in in-demand skills in cybersecurity, PCI DSS Compliance, Payment ecosystems, and more. Hurry! Grab this golden opportunity only on pwskills.com
Man in the Middle attack FAQs
Q1. What is an MITM attack?
Ans: An MITM attack or a Man-in-the-Middle attack is a type of cyberattack in which the attackers steal your personal, confidential or sensitive information by eavesdropping on communication between two or more people online.
Q2. What is the difference between MITM and Phishing?
Ans: MITM attacks are a new form of phishing. In these attacks, your information isn't gone but your messages are altered in real-time.
Q3. Does VPN protect from Man-in-the-Middle attacks?
Ans: Yes. If you are using VPN, then it can help in the protection from MITM attacks. This will also allow you to use public Wi-Fi without any worry, securely.
Q4. Can firewalls stop MITM attacks?
Ans: Yes. Firewalls that have encryption capabilities can help in detecting and preventing MITM attacks. It includes especially those that support SSL (Secure Sockets Layer) inspection.

