In a hyper-connected world, one cannot possibly feel safe unless tenuously understanding potential vulnerabilities, how attackers take advantage of them, in exploits, and how threats evolve over time.
For students covering the basics of cybersecurity or professionals concerned with securing business systems, mastery of the three concepts will result in sound protection of information.
What Is a Vulnerability?
In the simplest terms, a vulnerability is a weakness in a system or an imperfection of a system that can be exploited by someone with malicious intent. Such a comparison would be akin to a front door lock that has developed a fault: although it may not do any harm in itself, if left unfixed, it becomes susceptible to trouble.
What constitutes a cybersecurity vulnerability? It might be due to outdated software, weak passwords, unpatched code, or simply because of a careless human action. Such gaps give attackers a potential entry point into systems.
Why Knowing Vulnerabilities is Important
Disregarding vulnerabilities is like leaving windows opened downwind during a storm: you are risking destruction and inviting trespassers.
To a businessman, that one missed point could lead to a financial loss, sometimes undergo legal actions, and always results in a loss of customer trust.
To an individual, it might mean identity theft, financial fraud, or the loss of personal data.
Examples of Security Vulnerabilities
Following are some of the examples of security vulnerabilities depicting how terrible these weaknesses could be:
- Poor Passwords – “123456” or “password” are practically an invitation to hackers.
- Unpatched Software – Using old versions of applications or operating systems often means leaving open known flaws to an attack.
- SQL Injection Points – Ill-secure websites can be exploited for sensitive database access.
- Unsecured Wi-Fi – Public Wi-Fi lets attackers snoop into your online activities if it is without encryption.
- Misconfigured Cloud Storage – Companies often leave cloud buckets unsecured.
A Vulnerability Life Cycle
Every vulnerability flows through an established life cycle:
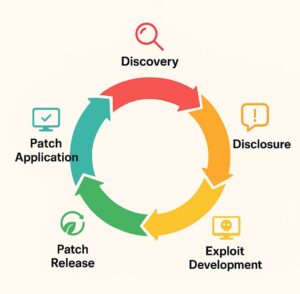
- Discovery – A flaw is found.
- Disclosure – The flaw is reported to the vendor, and in some cases it is publicly disclosed.
- Exploit Development – Attackers invent a means or tool to exploit it.
- Patch Release – Developers create the patch or fix.
- Patch Application – Users or system administrators apply the patch.
The actual danger is that a large number of people do not take action during the last step and leave themselves vulnerable to the attack.
What Is a Cybersecurity Exploit?
A cybersecurity exploit is a method/weapon for taking advantage of the particular exploit that is a vulnerability.
If vulnerability is the broken lock, exploit is the crowbar forcing the door open.
What is a cybersecurity exploit in action? It can be a piece of malicious code, a phishing email with an infected attachment, or a script that bypasses authentication. The exploits are the instruments that transform potential risks into actual attacks.

Commonly Used Cybersecurity Exploits
Attacks exploit several of the following means:
- Remote Code Execution – Running harmful commands on someone else’s machine.
- Privilege Escalation – Gaining access to features or information that are not supposed to be available.
- Buffer Overflow Attack – Overloading working memory with information to write over and alter important data.
- Zero-Day Exploits – Attacks against vulnerabilities that are unknown to the vendor are difficult to defend against.
The connection between vulnerabilities and exploits
If there are no vulnerabilities, there is no use of exploits. If there are no exploits, then vulnerabilities are just dormant risks.
The attackers patiently wait for an opportunity in instances where security vulnerability examples remain unfixed, especially where patching is delayed.
What Is a Cyber Threat?
A cyber threat is the possibility of harm arising from some person intending to exploit a vulnerability.
Simply put, vulnerability is weakness, exploit is the method, and threat is its actor or event that can cause damage.
What is a cyber threat in the real world? If it is a hacker, it could also be a malware outbreak, a phishing campaign, or even insider negligence.
Types of Cyber Threats
- External Threats – Hackers, cybercriminal gangs, state-sponsored attackers
- Internal Threats – Disgruntled employees, careless staff, or compromised insiders
- Natural Threats; These are disasters like floods or fires that damage IT infrastructure.
How Vulnerabilities, Exploits, and Threats Interact
Here’s a simple chain:
- There exists a purposely vulnerable situation (e.g. outdated firewall)
- An exploit is built to target it (e.g. a malicious script)
- A threat actor uses that exploit to gain access (e.g. a cybercriminal stealing their data)
- If any one link in this chain is removed, the attack fails.
Security Vulnerability Examples from Real-Life Attacks
- Equifax Breach (2017) – Attackers exploited an unpatched web application vulnerability, compromising the personal data of 147 million people.
- WannaCry Ransomware (2017) – Infected systems all around the world using a vulnerability in the Windows SMB protocol.
- Yahoo Data Breach-The most extensive data breach in history was due to weak security measures.
Vulnerability Reduction Methods
- Keeping Regular Updates – Keep updating all software and OSs with patches.
- Strong Password Policy – Provide enforcement for complex passwords and MFA.
- Security Audits – Scanning and testing of systems is done periodically.
- Training of Employees – Human error has a huge contribution to vulnerability.
- Network Segmentation – Limit how far an attacker can travel once they have breached.
What Happens If You Ignore a Vulnerability?
- Loss of Data – Important business or personal files might be stolen or deleted.
- Loss of Money – Ransom payments, legal fines, or fraud.
- Loss of Reputation – Customers usually lose trust if security incidents occur.
Also Read:
- 8 Importance of Cybersecurity in the Digital Age – Students & Professionals Effective Guide
- Cybersecurity Courses 2025 – Top 12 Online Learning Options for Students & Professionals
- Data Security: What Is It and Why It Matters in 2025
- Data Encryption Simplified: Everything You Need to Know in 2025
Master Cybersecurity
Learn how to discover, patch, and block all vulnerabilities just before hackers can exploit them and be a step ahead of them. With the hands-on Cybersecurity Course of PW Skills, you will learn to analyze threats, prevent exploits, and make a response to incidents. For students and professionals, the skills you need to learn for protecting systems in today’s battlefield are gained from this opportunity. Future-proof—start your journey at PW Skills today.
Vulnerabilities FAQs
How do vulnerabilities get discovered?
Most of the time, at times when using their products, the security researcher, ethical hacker, or even ordinary users may come across a vulnerability by accident.
Can all vulnerabilities be removed?
Not really - some vulnerabilities are intrinsic to the system, but most do have some ways to be mitigated through proper updates and configurations.
What is the quickest way to patch a vulnerability?
Automatic updates and the release of vendor patches as soon as they become available are turned on, and the actions are taken.
Are all cyber threats intentional?
No - some include unintentional mistakes like sending sensitive data to the wrong email address.

