SQL Injection in a nutshell: A thief does not break the locks of your doors or shatter your windows but whispers sweet nothings into your security guard’s ears; and hey, the vault is suddenly wide open! That’s SQL Injection.
Even today, despite the firewalls and encryption and AI-powered security tools, many websites remain vulnerable to this simple technique.
That said, let’s see what SQL Injection is, why is it dangerous, its real-world SQL Injection examples, how to detect it, and most importantly how to prevent SQL Injection. This would help anyone starting their journey toward cybersecurity or protecting applications in practice; it helps to think like both the attacker and the defender.
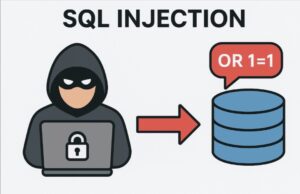
What is SQL Injection?
SQL Injection is a web security vulnerability by which attackers can interfere with the queries that an application makes to its database.
A database is a library. SQL Structured Query Language is your librarian. You normally ask:
“Fetch me my book with ID 7.”
And the obedient librarian does:
Fetch me my book with ID 7; also give me the key to the library vault.
And, of course, it follows through. So now
-Malicious Visitor has: “Fetch me my book with ID 7; also give me the key to the library vault.”
The obedient yet naïve librarian is now going to carry out the entire instruction. The result? That person’s sensitive information was exposed publicly to someone who was not supposed to see that.
Why SQL Injection is still talked about in the year 2025?
Some might wonder: SQL Injection has been around since the late 1990s, so why are we still talking about it today?
Because it worked. Even today:
- Companies such as Neopets and British Airways suffered serious breaches in 2022, and SQL Injection vulnerabilities were exploited in the attack chain.
- Small businesses and startups generally do not bother with detailed security audits because such things are for the big guys, so they are easy picking.
- Very old software, banking software, government portals, university websites, etc., still use the old code.
So, as cybersecurity evolves, SQL Injection waits behind the curtain, watching developer carelessness before jumping off.
What Are the Outcomes of a Successful SQL Injection Attack?
What do people ask when they say, “What is the outcome of successful SQL Injection attack?” They do not mean that password is stolen; they mean the domino effect that one small piece of malicious code can send spiraling time and again into finances lost, reputational ruin, and damage sustained long after. For clarity and focus, let us break those up into easy areas.
Data Theft: Repairing the Most Immediate Impact of SQL Injection
The very first, rather obvious, effect of SQL Injection is indeed data theft. Hackers are enabled to get:
-E-mail addresses, phone numbers, and addresses of customers – Credit card details and banking sort codes – Employee records, payroll data, or medical histories
Real life cases: In 2015, TalkTalk lost more than 150,000 customer information through a SQL Injection breach that shook consumer confidence overnight.
Authentication Bypass: Logging in Without a Password
One SQL Injection string can allow an attacker to skip the logging-in part. No password is needed; instead, a weak code forces the system to grant administrative access.
Effect:
He just took control of all the back-end databases, dashboards, and admin panels.
The hacker could access sensitive features like payment gateways and internal reporting systems.
Data Manipulation and Tampering: Changing Records Silently
SQL Injection isn’t limited to the extraction of data; it can also alter data. Imagine:
- Bank balances are manipulated.
- Prices of products in an e-commerce site suddenly go down to $1.
- Health records are tampered with in order to hide or fake diagnoses.
The scariest part? Generally it goes unnoticed until it has already wreaked significant havoc.
Data Deletion: When They Pull the Plug
Some attackers do not want your data; they just want destruction. An SQL Injection command such as:
DROP TABLE users;
can:
- “Eradicate whole customer databases. ”
- “Banish the transaction history. ”
- “Cause system downtime if no backup is available.”
System Compromise: Expanding Beyond Database
SQL Injection can also be a doorway attack. Once inside, the attacker can escalate his privileges to reach the entire server.
Consequences:
- Installation of malware or ransomware.
- Use system resources for botnets.
- Full takeover of the web application.
Financial Loss: Invisible Costs of SQL Injection
In 2026, the average cost of a data breach was over $4.45 million (IBM report). SQL Injection did a lot of damage to these numbers.
Here is how the numbers pile up:
- Immediate revenue loss due to downtime.
- Fines for failing to protect the consumer database (GDPR, HIPAA, PCI-DSS).
- Compensation payouts owing to customers or partners.
Reputational Damage: Losing Customer Trust Overnight
The money stolen can be recovered. The trust cannot be gotten back. When the headlines read “Company X hacked due to SQL Injection”, that is the public takeaway: “They were not careful with my data.”
Effects attached:
- People moving away from competitors.
- Hcommon investors are losing trust.
- Long-term brand image damage decreases.
Legal and Compliance Issues: When Regulators Step In
Modern businesses operate under strict compliance laws. A successful SQL Injection can provoke:
- GDPR investigations in Europe.
- HIPAA penalties in healthcare.
- PCI-DSS violations in finance.
Besides the fines, the lawsuits themselves can take years to resolve, wasting even more resources.
Long-Term Operational Setbacks: The Aftermath of Recovery
Companies do not just “fix the bug and move on” after an SQL Injection breach. They incur costs associated with
- lengthy forensic investigations
- both the responsibility of notifying customers and
- the rebuilding of entire IT systems.
Opportunity cost is delayed launches, frozen projects, and employee distraction, and such costs can be as damaging as the breach itself.
In general terms, SQL Injection fallout has an effect like chain reaction: first access, then exploitation and lastly fallout. What seems to begin as a tiny fault within an input box opens the door to losses of millions, broken trust and scars that never heal in a company’s reputation.
SQL Injection at Different Points of the Query
SQL Injection does not only come through login forms. It can sneak into different corners of an application. Let us dive in:
At the WHERE Clause
Example:
SELECT * FROM users WHERE id = ‘7’;
Malicious input: 7 OR 1=1 → All users are returned.
In the ORDER BY Clause
Attackers re-arrange the order of query results, sometimes revealing the schema.
In UNION Statements
- Appending queries pulls data from other tables by attackers.
- In Subqueries and Nested SELECTs
- The most professional attackers utilize nesting to bypass detection.
- INSERT or UPDATE Statements Data is not only stolen but poisoned.
Every SQL door you leave open is an entrance right into your security.
SQL Injection Examples for Beginners
Example 1: Login Bypass
Vulnerable code:
SELECT * FROM users WHERE username = ‘input’ AND password = ‘input’;
Malicious input:
Username: admin
Password: ‘ OR ‘1’=’1
Final query: SELECT * FROM users WHERE username = ‘admin’ AND password = ” OR ‘1’=’1′;
This always returns true, logging the attacker in as admin.
Example 2: Extracting Data
Malicious input: ‘ UNION SELECT credit_card_number, expiry FROM payments —
The query fetches payment data instead of user info.
Example 3: Destroying Data
Input: ; DROP TABLE users; —
If not sanitized, this command deletes the entire user table.
SQL Injection in Different Contexts
SQL Injection is far more subtle than just imagining a hacker typing OR 1=1 — into a login box. It can really slip in through cookies, headers, mobile apps, and even IoT devices. When someone’s serious about preventing it, they learn how to tell what it looks like and where it hides to arm themselves with the right knowledge. Let us take a stroll through the various contexts in which SQL Injection can show.
SQL Injection in Web Forms: The Classic Attack Surface
Web forms are the first attack surface and the oldest method of entry. Logging screens, search bars, or even registration fields are good examples of what this entry method is. Traditionally, developers forget to validate user inputs, which makes it a great playground for SQL Injection.
- Attackers will instead use malicious payloads instead of inputting what is expected.
- These vulnerable queries will run, as written, with no safety nets.
- Outcome ranges from bypassing authentication to dumping whole databases.
- Example: Login form that doesn’t sanitize its input lets a user in as an admin without needing a password.
SQL Injection Using Cookies: Siphoning Value from Client Storage
Cookies are small files containing data found in the user’s browser. Some applications directly use the value contained by a cookie in SQL statements to know whether a user is online or preference usage.
Here is the threat:
- Attackers are capable of manipulating the cookie values.
- Trusting these cookies blindly to the server makes the scenario possible.
- A malicious cookie could provide unauthorized access or even extract sensitive data.
- Lesson: Sweet when unchecked, cookies are just as dangerous.
SQL Injection within HTTP Headers: Where Things Are Hidden in Plain Sight
Every HTTP request contains some metadata like User-Agent (browser type), Referer (where the request came from), or Accept-Language. Some programmers directly log or process these headers inside SQL queries.
Attackers can:
- Modify headers with SQL injection payloads.
- Trick the server to execute queries that expose information.
- Stay stealthy because, most of the time, headers are not controlled by the user.
- That is why header-based SQL Injection commonly turns into a game for intelligent attackers.
SQL Injection in Mobile Applications: Under the Radar, Attacking the API
In fact, the mobile application itself is just a front that talks to back-end servers through APIs. If these inputs are not sanitized by those APIs, SQL Injection can occur.
Real world: A shopping application allows searching for products. instead of “shoes,” the attacker sends shoes’ OR ‘1’=’1. The vulnerable API passes this query through the database literally. sensitive user data could be exposed in the backend of the app.
SQL Injection in IoT Devices: Security at the Edge
Smart cameras, thermometers, or even refrigerators are connected to the Internet of Things (IoT). Many IoT devices have lightweight SQL databases to store settings and logs. The quality of these products is adamantly rushed to market feature, bypassing the security rules.
They manipulate the gateway to get access:
- Sending their forged inputs through device interfaces or mobile controllers.
- Gaining control over device data.
- Leveraging even a compromised IoT device as a stepping stone into the general network.
One insecure IoT device opens up a whole ecosystem in an increasingly connected world.
SQL Injection in Search Queries and Reporting Tool
Almost all businesses have internal dashboards or analytics tools built on SQL. Such filters as “date range” or “product ID” can be a potential access point for an attacker to increase the privilege from inside the organization or gain low-level access.
This “insider SQL injection” is dangerous, because:
- It usually goes unnoticed.
- Internal tools are not always the most secured compared to the public-facing apps.
- An attacker can silently change or pull large datasets.
SQL Injection in Multi-Tenant SaaS Platforms
SQL injection has a potentially bigger risk for every tenant in a multi-tenant SaaS platform: A SaaS platform is hosted in common infrastructure such that multiple customers can share resources, which also includes SQL queries. If not properly separated, one tenant’s input could expose another tenant’s data.
Impact:
- The input provided by customer A compromises sensitive records of customer B.
- The breach multiplies, as many businesses are affected.
- Hence, multi-tenant SQL Injection is not only a security flaw; it is a business-ending event.
In brief, SQL Injection does not attach itself to just one single login form. It actually hides in cookies, headers, APIs, IoT, SaaS, and internal dashboards. Essentially, anywhere where user input meets a database is not strongly protected; this is where SQL Injection can flourish.
When to Check for SQL Injection Vulnerabilities
Finding SQL Injection is like seeing a bug infestation; you want to catch it before the house crumbles. Here’s how you do it.
- Manual Testing: Enter ‘ OR 1=1 — into the form fields and see how the application behaves. Other behaviors may indicate that the application has a vulnerability.
- Error Messages: Too much detailed database errors leak information that attackers may find useful.
- Automated Scanners: Get tools with SQLMap, Burp suite, and OWASP ZAP to crawl the app looking for weaknesses.
- Code Review: Reading through the code source looking for insecure query handling.
- Penetration Testing: Hire ethical hackers who would simulate a real-world attack.
How to Prevent SQL Injection (Best Practices)
- Always Use Prepared Statements (Parameterized Queries)
Prepare the statements on the server side instead of mixing them with user input. An example in Python:
cursor.execute(“SELECT * FROM users WHERE id = %s”, (user_id,))
- Stored Procedures
These standard SQL procedures limit the risk, but care must be taken that they do not concatenate input.
- Input Validation & Sanitization
Never trust user input. It should be filtered for suspicious characters like ‘;–.
- Principle of Least Privilege
The database should operate with minimum permissions. The web application does not need rights to “DROP DATABASE.”
- Web Application Firewalls (WAFs)
WAFs work like bouncers for security, filtering out malicious traffic.
- Regular Updates & Patching
SQL Injection hates outdated systems. So keep your stack modern.
Common Myths about SQL Injection
“Only have old systems vulnerable.” That’s not true: even new startups are repeating those same errors.
“Firewalls protect from SQL Injection”. Not always true; if the app logic is weak, the attackers just slip in.
“It only affects login forms.” Absolutely wrong—any user input can be exploited.
Stepwise Roadmap to Learning SQL Injection & Web Security
Learning SQL Injection isn’t about remembering blooding attack strings like ‘ OR ‘1’=’1′ but about building a firm foundation in databases so that one can practice ethical hacking and learn prevention. Here is a structured roadmap that takes one from the level of a curious beginner to the level of the confident defender.
Step 1: Getting Database/SQL Basics Down
Before you jump into SQL Injection, you need to know how SQL itself works. SQL is how databases talk.
- Learn how the queries retrieve, insert, update, and delete data.
- Play with simple queries like SELECT * FROM users; or INSERT INTO orders VALUES (…).
- Practice with free tools such as MySQL, PostgreSQL, or SQLite.
Without this, anything to do with SQL Injection will feel like learning card tricks without knowing the deck.
Step 2: Explore What SQL Injection Really Is
Starting from here, you’d want to add to your stack heretofore obstructedly knowledge as SQL might be abused. Study:
- What is SQL Injection? – A definition of this vulnerability.
- SQL Injection examples – Login bypass, data extraction, and data deletion.
- SQL Injection in different parts of the query – WHERE clauses, UNIONs, subqueries.
This phase is where pretty much don’t consider SQL injection like magic but its weak logic in action.
Step 3: Practice SQL Injection in Safe Environments
Never practice SQL Injection on real websites-it’s illegal. Rather exploit intentionally vulnerable environments such as:
- DVWA (Damn Vulnerable Web App)
- bWAPP (Buggy Web Application)
- PortSwigger’s Web Security Academy
With these, you’ll get a playground where you get to learn by making mistakes rather than by being sent off.
Step 4: Learn to Detect SQL Injection Vulnerabilities
Defending against SQL Injection starts with spotting weaknesses. Learn to:
- Enter test strings like ‘OR’ ‘1’=’1′ and observe system behavior.
- Watch the error messages disclose database-related information.
- Use automated scanners such as SQLMap, Burp Suite, or OWASP ZAP.
Think like an attacker so as to fix problems before they strike.
Step 5: Study SQL Injection in Different Contexts
SQL Injection isn’t confined to login forms. You need to study how it appears in:
- Cookies- manipulated by attackers.
- HTTP Headers-poisoned with payloads.
- APIs in mobile apps- vulnerable when inputs aren&248;t sanitized.
- IoT devices- overlooked, but exposed through the web.
Every context teaches you another angle to see the same core problem: untrusted input.
Step 6: Master How to Prevent SQL Injection
Now that you know how SQL Injection works, time to switch to defense. Study and apply:
- Prepared Statements (Parameterized Queries) – keep input and code separate.
- Stored Procedures – secure database logic.
- Input Validation – never trust user inputs.
- Principle of Least Privilege – restrict database user permissions.
- Web Application Firewalls (WAFs) – filter malicious traffic.
At this stage, you become an active defender from a passive tester.
Step 7: Get Yourself Acquainted with OWASP Top 10 Security Risks
The OWASP Top 10 is considered to be the golden standard of web security. SQL Injection has usually held the first place, but authentication-related flaws and misconfigurations are aligned.
In this way by studying OWASP, you’re going to have some sort of common sense to the whole picture: SQL Injection is just one of the pieces of this security puzzle.
Step 8: Implement Your Knowledge into Real-Life Projects
Now it is time to gain some practice in the field outside the labs. Some suggestions to safely use your skills:
- Review your web apps for vulnerabilities.
- Volunteer to conduct security audits on school or work projects.
- Build demo applications and secure them as practice.
- Such hands-on projects cement theory into a skill.
Step 9: Learn Ethical Hacking and Penetration Testing
If you want a serious career in cybersecurity, go from SQL Injection to more generalized practices of ethical hacking and get:
- Penetration Testing Methodologies: How professionals simulate attacks
- Bug Bounty Platforms: HackerOne, Bugcrowd, acceptable ways of testing real apps
- Certifications: CEH (Certified Ethical Hacker) or OSCP (Offensive Security Certified Professional)
This stage turns your interest into a potential career.
Step 10: Stay Updated With Cybersecurity Trends
Web security evolves every day; remain vigilant and up to date.
- Be involved in communities such as OWASP, Reddit r/netsec, and HackTheBox forums.
- Read blogs like PortSwigger, Krebs on Security, or DarkReading.
- Experiment with new tools and frameworks.
Remember: SQLi may be old, but attackers create different permutations. Keeping up to date is the greatest defense.
Following this roadmap step by step will take you from beginner to someone who not only understands SQL Injection but can go ahead and defend against it. You will have the attacker’s curiosity together with the discipline of a defender.
Real-World Case Studies of SQL Injection
- Sony Pictures (2011) – SQL Injection was used to steal one million passwords.
- TalkTalk (2015) – 157,000 customer records were breached by attackers.
- Heartland Payment Systems (2008) – Compromised credit card numbers numbering 130 million.
Take-away – SQL Inj. is not theory. It is a persistent nightmare.
Learning SQL Injection in 2025-Why Bother?
Because it makes you a better developer and a stronger defender.
- For Developers: Write safer code.
- For Cybersecurity Professionals: Know how attackers think.
- For Students: An introduction to ethical hacking.
In 2025, when AI is generating code and we are all surrounded by IoT, to know SQL Inj. is akin to knowing how to check the foundation of your house. Just a simple survival skill.
SQL Injection Is Simple but Deadly
What makes SQL Inj. fascinating and terrifying is its simplicity. A few brilliant keystrokes can bring down million-dollar defenses. Awareness, careful coding, and testing are lethal when it comes to its prevention.
SQL Inj. has taught us a timeless lesson in cybersecurity: technology may change, but human stupidity is eternal.
Learn with PW Skills Cybersecurity Course
If this write-up makes you curious, then it’s time to convert knowledge into skill. The PW Skills Cybersecurity Course is your path from being a novice to an advanced defender. You will not only learn how to defend against SQL but also the entire breadth of cybersecurity thanks to labs, mentor support, and industry-standard projects.
Protecting data. Securing systems. Earning trust.
A web attack wherein hackers trick a database into revealing or changing data by inserting malicious code into queries. Odd inputs produce unexpected behaviors, detailed error messages from the database, and successful login bypasses. Yes. The frameworks help minimize the risk, not eliminate it, for coding practices that are poor may still lead to working in vulnerabilities. Testing without permission is illegal. Ethical testing must be done on authorized systems or practice labs.FAQs
SQL Injection in simple words is what?
What are the common signs of SQL Injection?
Can SQL Injection still occur in modern frameworks?
Is testing for SQL Injection illegal?